hellreturn
Management-
Posts
2837 -
Joined
-
Last visited
-
Days Won
53
Content Type
Forums
Profiles
Events
Gallery
Downloads
Articles
Everything posted by hellreturn
-
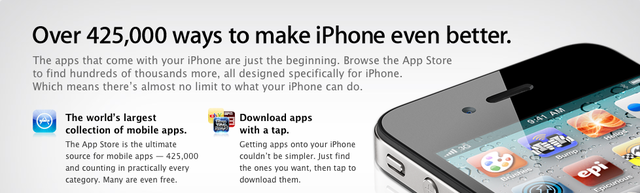
In a press release today, Apple has announced that their iOS App Store has reached a total of 15 billion downloads. Quote The one billionth app, Bump created by Bump Technologies, was downloaded by Connor Mulcahey, age 13, of Weston, CT. As the grand prize winner of Apple’s one billion app countdown contest, Connor will receive a $10,000 iTunes® gift card, an iPod® touch, a Time Capsule® and a MacBook® Pro. “The revolutionary App Store has been a phenomenal hit with iPhone and iPod touch users around the world, and we’d like to thank our customers and developers for helping us achieve the astonishing milestone of one billion apps downloaded,” said Philip Schiller, Apple’s senior vice president of Worldwide Product Marketing. “In nine months, the App Store has completely revolutionized the mobile industry and this is only the beginning.” Today, the groundbreaking App Store has more than 35,000 applications available to consumers in 77 countries, allowing developers to reach tens of millions of iPhone™ and iPod touch users around the world. This summer the iPhone OS 3.0 software update will provide developers with over 1,000 new developer APIs enabling In-App Purchases, Peer-to-Peer connections, App control of accessories, and Push Notifications. The iPhone OS 3.0 release will also add over 100 customer features including cut, copy and paste; Spotlight™ search; landscape keyboard and view for all key iPhone apps; MMS* support; and expanded parental controls for apps, TV shows, and movies from the App Store. *MMS messaging is available only on iPhone 3G; fees may apply. MMS may not be available in all areas. Apple ignited the personal computer revolution in the 1970s with the Apple II and reinvented the personal computer in the 1980s with the Macintosh. Today, Apple continues to lead the industry in innovation with its award-winning computers, OS X operating system and iLife and professional applications. Apple is also spearheading the digital media revolution with its iPod portable music and video players and iTunes online store, and has entered the mobile phone market with its revolutionary iPhone. The highly popular software and content delivery ecosystem opened on July 18, 2008 and, according to Apple, took nine months to reach its first billion downloads. Since then, things have accelerated. Last month at Apple's World Wide Developer's Conference, Jobs announced that the App Store had achieved 14 billion downloads. That means one billion downloads were reached in just a month's time. This makes the App Store the single most successful mobile software distribution environment to date. And it's easy to see why. According to today's press release, the 15 billion downloads have been spread across 200 million iDevice users all across the world. That translates into 75 app downloads per user. At present, there are over 425,000 apps available for iOS devices in the App Store, with 100,000 of these specifically designed for the company's extremely successful iPad tablet. Compare that to iOS's biggest competitor Android's estimated 4.5 billion downloads as of May 2011 which is the most recent official figure available. Google claims that over 100 million Android devices have been activated meaning 52 apps have been downloaded per user. At present, it's estimated there are over 200,000 apps available in the Android Market. Source: Apple Click here to view the article
-
The space shuttle Atlantis is set to launch on Friday, July 8 at 11:26 a.m. EDT from Cape Canaveral, Florida. This will not only be the final launch for the Atlantis, but also the final launch of the entire space shuttle program. After this mission, the shuttle fleet will be officially retired, and NASA will begin to focus on new ways to send humanity into space. The launch of the shuttle is in question, as NASA weather officials give only a 30% chance for favorable weather on Friday. That hasn't stopped the pre-launch countdown, however, as astronauts continue their routines to prepare the shuttle for launch. If there is a delay in the launch of the shuttle, we can expect it to last anywhere from a day to a week. The best place to catch the shuttle launch online will be from NASA TV's home page. You can see the live stream of the shuttle's entire launch and even watch it later if you miss the launch. NASA also has a uStream page for NASA TV, which you can watch on your iPhone with the Ustream app.
-
In a press release today, Apple has announced that their iOS App Store has reached a total of 15 billion downloads. The highly popular software and content delivery ecosystem opened on July 18, 2008 and, according to Apple, took nine months to reach its first billion downloads. Since then, things have accelerated. Last month at Apple's World Wide Developer's Conference, Jobs announced that the App Store had achieved 14 billion downloads. That means one billion downloads were reached in just a month's time. This makes the App Store the single most successful mobile software distribution environment to date. And it's easy to see why. According to today's press release, the 15 billion downloads have been spread across 200 million iDevice users all across the world. That translates into 75 app downloads per user. At present, there are over 425,000 apps available for iOS devices in the App Store, with 100,000 of these specifically designed for the company's extremely successful iPad tablet. Compare that to iOS's biggest competitor Android's estimated 4.5 billion downloads as of May 2011 which is the most recent official figure available. Google claims that over 100 million Android devices have been activated meaning 52 apps have been downloaded per user. At present, it's estimated there are over 200,000 apps available in the Android Market. Source: Apple
-
If anybody needs it, feel free to PM me.
-
Google will no longer allow users to have private Google profiles after July 31st, reports Search Engine Land. The company had previously allowed users to create and maintain profiles on its service without publicly disclosing their existence. Google is making the change primarily to aid in the growth of its new Google+ social network. This change means that you must have at least your full name and gender shown publicly to join Google+. Google updated its public profiles page some time ago, as we commented on, to notify users of this upcoming change, stating: Quote The purpose of Google Profiles is to enable you to manage your online identity. Today, nearly all Google Profiles are public. We believe that using Google Profiles to help people find and connect with you online is how the product is best used. Private profiles don’t allow this, so we have decided to require all profiles to be public. Keep in mind that your full name and gender are the only required information that will be displayed on your profile; you’ll be able to edit or remove any other information that you don’t want to share. If you currently have a private profile but you do not wish to make your profile public, you can delete your profile. Or, you can simply do nothing. All private profiles will be deleted after July 31, 2011. This change makes sense in the context of Google+ being a network that defaults to a ‘public’ setting, somewhat like Twitter. Anything that you share can be moderated to only appear to a member of the exact circles that you choose, but by default, everyone sees everything. There are still some controls that are available to users, regardless of the public status of their profile. Users of Google can still choose to have their profile not be included in search results pages by visiting their profile privacy settings and changing the ‘Search visibility’ option. One nice feature that Google does give users is the ability to remove their profile from showing in Google search. By going to your account page, you can uncheck the “Help others find my profile in search results” button to be removed from the results pages. Click here to view the article
-
Silent Community Server
hellreturn replied to hellreturn's topic in Clans / Guilds and Gaming Communities
AFAIK Server is up and running but not many players where interested. -
Google will no longer allow users to have private Google profiles after July 31st, reports Search Engine Land. The company had previously allowed users to create and maintain profiles on its service without publicly disclosing their existence. Google is making the change primarily to aid in the growth of its new Google+ social network. This change means that you must have at least your full name and gender shown publicly to join Google+. Google updated its public profiles page some time ago, as we commented on, to notify users of this upcoming change, stating: This change makes sense in the context of Google+ being a network that defaults to a ‘public’ setting, somewhat like Twitter. Anything that you share can be moderated to only appear to a member of the exact circles that you choose, but by default, everyone sees everything. There are still some controls that are available to users, regardless of the public status of their profile. Users of Google can still choose to have their profile not be included in search results pages by visiting their profile privacy settings and changing the ‘Search visibility’ option. One nice feature that Google does give users is the ability to remove their profile from showing in Google search. By going to your account page, you can uncheck the “Help others find my profile in search results” button to be removed from the results pages.
-
"A lot of the guys working on Modern Warfare 3 are the same guys who worked on Modern Warfare 2 and Modern Warfare," the executive said to IndustryGamers. "A lot of them are Infinity Ward sort of lifers and have been there from the beginning." Some have questioned Infinity Ward's credit following the forced departure of studio leads Frank West and Vince Zampella, along with an unknown number of colleagues, now at the ReSpawn Entertainment. "A lot of the turmoil, it all happened before I got here, so I never got to work with the old Infinity Ward," Hirshberg admitted. He continued, "I only got to work with the new Infinity Ward, and all I can tell you is while they went through a huge transition, and while there was a lot of rebuilding that had to happen and they had to bring in some new talent to replace some of the people that had left, this is one of the most dazzlingly creative group of people I've ever met in my life. And so anyone who tells you, 'This is not the real Infinity Ward' is wrong. This is an unbelievable developer, an unbelievably talented studio… and they've got something to prove, too. I think they've taken a lot of pride in proving the skeptics wrong and so far, the reception of Modern Warfare 3 has been pretty great." Sledgehammer is on board Modern Warfare 3, but Hirshberg told the game is benefiting, rather than suffering, from more than one cook eyeing the broth. Hirshberg added, "They welcomed in a partner and that was probably a decision born out of necessity – nobody probably would have designed it that way proactively, but because they were going through a rebuilding right in the middle of this development, they welcomed a pretty high octane partner into their creative process." "And Sledgehammer truly has treated them as partners, and the game is a reflection of a combined vision between those two studios. And to my great delight it is a one plus one equals three situation. The game has gotten better because of these two very strong, creative forces working together," he explained. Modern Warfare 3 is expected in November.
-
This is so nerd vs nerd Looks like luz boat is sinking like titanic.
-
A group calling itself the A-Team has posted what they contend are the names, locations, aliases and even family members of the hacking cabal known as Lulz Security. Could this be the real reason the high-profile hacking group disbanded this weekend? Listening to A-Team tell the story, there is no love lost between this new hacking crew and whoever it is ends up being the real people behind now-disbanded group LulzSec (and related group gn0sis): The timing of this data dump and abrupt the Lulz Security "retirement" Saturday are indeed curious. I suppose if a number of high-profile arrests are made in the near future concerning teens and twenty-something computer experts we'll know if this list is legit or not, huh? The full A-Team's message can be found here: http://pastebin.com/raw.php?i=iVujX4TR
-
Video game developer Valve has announced that "Team Fortress 2" will become entirely free to play for PC and Mac customers. Robin Walker of Valve assured that "Team Fortress2" will not have any pay-to-win options, premium subscriptions or advertising models. It will be completely free, with the exception of in-game items. In-game purchases will be the only way Valve will make any money from "Team Fortress 2." http://www.youtube.com/watch?v=eQ8duKs2Plw You can download it for free from official Steam site: http://store.steampowered.com/app/440/ PC System Requirements: Minimum: 1.7 GHz Processor, 512MB RAM, DirectX® 8.1 level Graphics Card (Requires support for SSE), Windows® 7 (32/64-bit)/Vista/XP, Mouse, Keyboard, Internet Connection Recommended: Pentium 4 processor (3.0GHz, or better), 1GB RAM, DirectX® 9 level Graphics Card, Windows® 7 (32/64-bit)/Vista/XP, Mouse, Keyboard, Internet Connection PS. Please, don't forget about ET while enjoying TF2
-
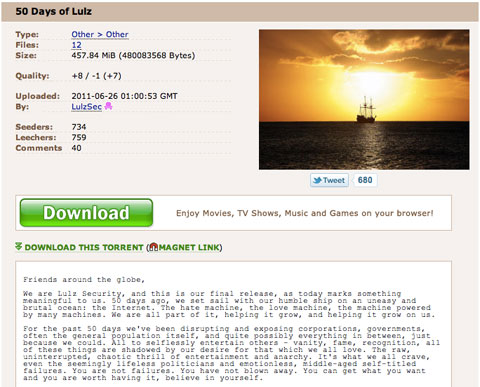
Lulz Security, a group of hackers who have tormented corporations and government agencies, said Saturday that it would stop its spree, 50 days after it first started attacks. In a statement posted on The Pirate Bay, a file-sharing Web site, the group said its six members had decided to "say bon voyage" as Lulz Security but did not cite a reason. In addition, the group shared a number of files and documents it said were obtained in the course of its attacks. These files, which were available for download, included what appeared to be internal company documents from AT&T and user names and passwords from a number of other Web sites. On its Twitter feed, the group's members encouraged other hackers to continue attacking Web sites and government agencies and said they planned to stay involved in the efforts through Anonymous, another collective of rogue hackers. It is unclear why the group decided to stop hacking under its current name. In a recent interview with Adrian Chen of Gawker, one the group's members, who goes by the name "Topiary" online, said Lulz Security planned to continue its campaign for some time and said he had no fears of being apprehended by the authorities. The full statement posted on The Pirate Bay by Lulz Security:
-
How to edit player level in silent database.
hellreturn replied to RaNeR's topic in General Discussion
For spawn times, add this in your etmain server config: set g_useralliedrespawntime 15 set g_useraxisrespawntime 15 -
Does the application get's auto installed in Android or it asks for your permission to install it?
-
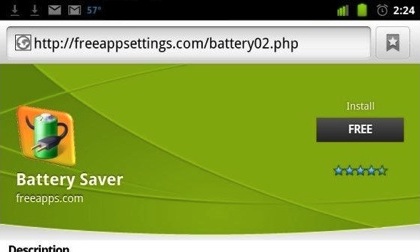
Lookout Security Firm as identified a new Android Trojan named GGTracker that is downloaded to a user’s phone after visiting a malicious webpage that imitates the Android Market. The Trojan then proceeds to sign up the user to premium SMS services without their knowledge. The Trojan targets only U.S. Smartphone users when they click on a malicious in-app advertisement. The website lures users to click-through to download and install an application one of which is a fake battery optimizer called "t4t.pwower.management", and another is a porn app called "com.space.sexypic". After the application has been installed, GGTracker registers the user for premium subscription services. The Trojan carries out this task by contacting another server in the background where the malicious behavior intercepts crucial confirmation data to charge users without their consent or knowledge. Lookout advises that users can protect themselves from malicious webpage’s by taking a few precautions: After clicking on an advertisement, make sure the page and URL matches the website the advertisement claims it’s sending you to. Download apps only from trusted sources. Also look at the developer’s name, reviews, and star ratings. If you are suppose to be on the Android Market, check the URL to make sure you are on the Market and not redirected to another site. Always monitor your phone for any unusual behavior like unusual SMS messages, strange charges on your phone bill or unusual network activity. Check all apps running in the background and investigate any that you think should not be running. Don’t download any third party apps by making sure "unknown sources" is not check off in "application settings" in your android system. Download a mobile security app for your phone that scans every app you download to ensure its safe. More information: Lookout Blog
-
Our old favorite browser just got some updates, Firefox 5 is released on Windows, Mac, Linux, and Android. It's the first release of Firefox's new three-month rapid release development cycle, in which the user can get new features, updates, and bug fixes faster than ever before. Although there are only small updates, and it looks like it cannot make any difference, well, think again. This small features really matters when combined together, they make a really significant change. Some changes maybe useful for other users while some might not think so, for example, the adopted feature from Google Chrome in which the tabs stay the same size when closing them. Normally when you have a ton of tabs open and then you close one, the other tabs will expand to fill the space that the closed one had occupied. Now, it only does resize when your mouse leave the tab bar, so you can close consecutive tabs easily without moving your mouse. Some great features added are: Support for CSS animation that lets page elements move around the screen. It's very useful to make web pages and web apps more dynamic. Do-Not-Track on Andriod, Mozilla created the Do-Not-Track feature to let users have control on how their browsing behavior is tracked and used on the web. Firefox new add-on SDK now lets developers build extensions with the use of HTML, CSS, and Javascript. This will make extensions easier to write and improve compatibility over the next versions of Firefox. Increased speed Improved stability Fixed security issues The internet is changing in a fast paced cycle, so browsers need to catch up with the growing needs of the users. This update indicates that Firefox is not falling behind of the browser wars, it still got some trump cards under its sleeves. Click here to view the article
-
Our old favorite browser just got some updates, Firefox 5 is released on Windows, Mac, Linux, and Android. It's the first release of Firefox's new three-month rapid release development cycle, in which the user can get new features, updates, and bug fixes faster than ever before. Although there are only small updates, and it looks like it cannot make any difference, well, think again. This small features really matters when combined together, they make a really significant change. Some changes maybe useful for other users while some might not think so, for example, the adopted feature from Google Chrome in which the tabs stay the same size when closing them. Normally when you have a ton of tabs open and then you close one, the other tabs will expand to fill the space that the closed one had occupied. Now, it only does resize when your mouse leave the tab bar, so you can close consecutive tabs easily without moving your mouse. Some great features added are: Support for CSS animation that lets page elements move around the screen. It's very useful to make web pages and web apps more dynamic. Do-Not-Track on Andriod, Mozilla created the Do-Not-Track feature to let users have control on how their browsing behavior is tracked and used on the web. Firefox new add-on SDK now lets developers build extensions with the use of HTML, CSS, and Javascript. This will make extensions easier to write and improve compatibility over the next versions of Firefox. Increased speed Improved stability Fixed security issues The internet is changing in a fast paced cycle, so browsers need to catch up with the growing needs of the users. This update indicates that Firefox is not falling behind of the browser wars, it still got some trump cards under its sleeves.
-
I don't think it's lulzsec this time. As per the news, it seems 2 new hackers.. Sony needs internal security audit on all there websites tbh
-
While there have been cyber attacks made against other companies and government organizations in the last couple of months, Sony has been by far the company that has suffered through the most attacks. Today CNet's News.com reports that yet another web site owned and operated by one of Sony's divisions has been attacked. Two hackers claimed they took over 177,000 emails from the Sony Pictures France web site. The two hackers who accomplished the attack said they got through via an SQL injection. The duo posted 70 of the emails on a Pastebin web page. Sony Pictures has yet to confirm the attack saying only, "We are currently investigating this claim." One of the hackers, known as "Idahc", stated in a Forbes.com interview last week that he is launching these attacks as a way to get companies like Sony to improve their web site security systems. This is the 20th cyber attack on a web site or server owned and/or operated by the Japanese company in the past couple of months. Of course the biggest attack happened on April 20 when hackers attacked the Sony Playstation Network online gaming service. Sony said that tens of millions of PSN accounts were exposed although no financial info was apparently taken. Sony shut down the network for a few weeks and has only just recently brought the Playstation Network back to full operations. It also compensated PSN users for the system downtime with free downloadable games as well as other offers. Click here to view the article
-
Intel has now added three new high-efficiency, low-power parts to its product catalog. These will supposedly be the new chips for the MacBook Airs due a few weeks from now, according to Apple Insider. The ultra low voltage (ULV) are 17 watts, making them suitable for use in the ultra-thin MacBook Airs. The standard parts used by Apple consume 25-35 watts, making them unusable in the MacBook Air. The new lineup consists of three new parts. The Core i7-2677M is a dual-core processor that runs at 1.8 GHz, with TurboBoost 2.0 up to 2.9 GHz and a 4 MB cache. The Core i7-2637M is another dual-core part that runs at 1.7 GHz, with boosts up to 2.8 GHz and the standard 4 MB cache. The Core i5-2557M is a dual core part that runs at 1.7 GHz with boosts up to 2.7 GHz and a cache of 3 MB. The prices are 317, 289 and 250 US Dollars, respectively. Intel sees a huge market for ultra-thin notebooks like Apple's offerings. When the Air was fist released, it was criticized for not being thin enough and giving up too many features. Apple has since made the Air thinner and reduced the price, while adding a Solid State Drive, which supports very fast booting, wake, and program launching. One will have to see what is offered as Apple launches its MacBook Air refresh in the coming weeks. Click here to view the article
-
In a move aimed squarely against Skype and its new overlords, Google is taking voice chat and videoconferencing to the land of the free and open source. According to Cnet, Google is planning to add an open source communications protocol called WebRTC into future versions of Chrome. Google developed this project as an outgrowth of its purchase of Global IP Solutions in 2010, and released it to the open source community in May 2011. In typical Google form, the plan was to take Skype-like communication technologies and capabilities, and stick them on the web, in any browser. It promised to work with other browser developers to help achieve this goal, so that developers could start writing web apps that take advantage of the open standard. Google has already been in the multimedia teleconferencing game for some time. After releasing Voice and Video chat for its Gtalk client, re-releasing it in a mobile incarnation, and integrating its Google Voice VoIP product into new versions of Android OS, Google is ready to unleash its model on non-proprietary platforms. Microsoft likely already has plans to heavily integrate Skype into many of its online services. If WebRTC can take off as a viable project that developers will want to use, Microsoft could see some stiff competition from developers looking for open-source and cross platform communications solutions in their web apps. Ultimately, the platform could be used to build a total Skype replacement. WebRTC is Google’s latest attempt to bring native app capabilities to the cloud. As demonstrated in Chrome OS, Google is confident that most if not all activities done by users on a regular basis can be done from a web app. The same applies for real time multimedia communication, and WebRTC hopes to streamline and open source that goal. Source: Neowin Click here to view the article
-
While there have been cyber attacks made against other companies and government organizations in the last couple of months, Sony has been by far the company that has suffered through the most attacks. Today CNet's News.com reports that yet another web site owned and operated by one of Sony's divisions has been attacked. Two hackers claimed they took over 177,000 emails from the Sony Pictures France web site. The two hackers who accomplished the attack said they got through via an SQL injection. The duo posted 70 of the emails on a Pastebin web page. Sony Pictures has yet to confirm the attack saying only, "We are currently investigating this claim." One of the hackers, known as "Idahc", stated in a Forbes.com interview last week that he is launching these attacks as a way to get companies like Sony to improve their web site security systems. This is the 20th cyber attack on a web site or server owned and/or operated by the Japanese company in the past couple of months. Of course the biggest attack happened on April 20 when hackers attacked the Sony Playstation Network online gaming service. Sony said that tens of millions of PSN accounts were exposed although no financial info was apparently taken. Sony shut down the network for a few weeks and has only just recently brought the Playstation Network back to full operations. It also compensated PSN users for the system downtime with free downloadable games as well as other offers.
-
Intel has now added three new high-efficiency, low-power parts to its product catalog. These will supposedly be the new chips for the MacBook Airs due a few weeks from now, according to Apple Insider. The ultra low voltage (ULV) are 17 watts, making them suitable for use in the ultra-thin MacBook Airs. The standard parts used by Apple consume 25-35 watts, making them unusable in the MacBook Air. The new lineup consists of three new parts. The Core i7-2677M is a dual-core processor that runs at 1.8 GHz, with TurboBoost 2.0 up to 2.9 GHz and a 4 MB cache. The Core i7-2637M is another dual-core part that runs at 1.7 GHz, with boosts up to 2.8 GHz and the standard 4 MB cache. The Core i5-2557M is a dual core part that runs at 1.7 GHz with boosts up to 2.7 GHz and a cache of 3 MB. The prices are 317, 289 and 250 US Dollars, respectively. Intel sees a huge market for ultra-thin notebooks like Apple's offerings. When the Air was fist released, it was criticized for not being thin enough and giving up too many features. Apple has since made the Air thinner and reduced the price, while adding a Solid State Drive, which supports very fast booting, wake, and program launching. One will have to see what is offered as Apple launches its MacBook Air refresh in the coming weeks.
-
In a move aimed squarely against Skype and its new overlords, Google is taking voice chat and videoconferencing to the land of the free and open source. According to Cnet, Google is planning to add an open source communications protocol called WebRTC into future versions of Chrome. Google developed this project as an outgrowth of its purchase of Global IP Solutions in 2010, and released it to the open source community in May 2011. In typical Google form, the plan was to take Skype-like communication technologies and capabilities, and stick them on the web, in any browser. It promised to work with other browser developers to help achieve this goal, so that developers could start writing web apps that take advantage of the open standard. Google has already been in the multimedia teleconferencing game for some time. After releasing Voice and Video chat for its Gtalk client, re-releasing it in a mobile incarnation, and integrating its Google Voice VoIP product into new versions of Android OS, Google is ready to unleash its model on non-proprietary platforms. Microsoft likely already has plans to heavily integrate Skype into many of its online services. If WebRTC can take off as a viable project that developers will want to use, Microsoft could see some stiff competition from developers looking for open-source and cross platform communications solutions in their web apps. Ultimately, the platform could be used to build a total Skype replacement. WebRTC is Google’s latest attempt to bring native app capabilities to the cloud. As demonstrated in Chrome OS, Google is confident that most if not all activities done by users on a regular basis can be done from a web app. The same applies for real time multimedia communication, and WebRTC hopes to streamline and open source that goal. Source: Neowin
-
You can find all server variables from this link/manual. If g_misc is not added in config it will choose default value i.e. 0. If you like to modify the behavior, then you can add it in server config as: set g_misc 5 5 = 1 + 4 = Enable double jump and HP display. To store XP you need: set g_XPSave 23 set g_XPSaveMaxAge_xp "1d" set g_XPSaveMaxAge "30d" You need to set g_gametype in your map rotation config i.e. objectivecycle.cfg to enable map voting.